The following is a response to CVE-2022-45544 (2022-11-09) authored by Francisco Marinho, who claimed that there is an "Insecure Permission vulnerability in Schlix Web Inc SCHLIX CMS 2.2.7-2 [that] allows attacker to upload arbitrary files and execute arbitrary code." The analysis is incorrect due to the following reasons:
- You need an admin access and his proof of concept didn't demonstrate any unauthorized access to the Theme Manager within SCHLIX CMS.
- If you write a piece of code in the theme's index.php (e.g. system($_GET['tristao']) ) and upload it, of course you can execute it. In any PHP-based CMS where PHP code is allowed in the theme, you can write anything you want, including system ("rm -rf /") and this is NOT AN ERROR and there is NO UNEXPECTED BEHAVIOUR. You can test this with other PHP-based CMS such as Wordpress, Joomla, or Drupal and the behaviour is identical and this is NOT a vulnerability. If you want to disable a certain PHP function deemed dangerous, do it with disable_functions in php.ini.
- There is already a warning in the upload form that you should upload only from a trusted source. We're not responsible for any vulnerability caused by 3rd party plugins. See the second screenshot below.
Francisco's proof of concept, as described in https://github.com/tristao-marinho/CVE-2022-45544/blob/main/README.md and https://www.youtube.com/watch?v=_0X6AzXmhrU, is as follows:
- Login with your account
- Access the directory in url http://[examplewebsite].com/admin/app/core.thememanager
- Download theme Superhero in https://www.schlix.com/extensions.releases/action/download/filename/theme_superhero-1.1.zip
- Unzip theme_superhero-1.1.zip
- Edit file in path superhero/themes/superhero/index.php, adding "system($_GET['tristao']);" on line three.
- Our response: You can add any code here because it's a PHP script. You can execute system ("rm -rf /") or whatever and it will call the system(...) function unless you disable it via php.ini.
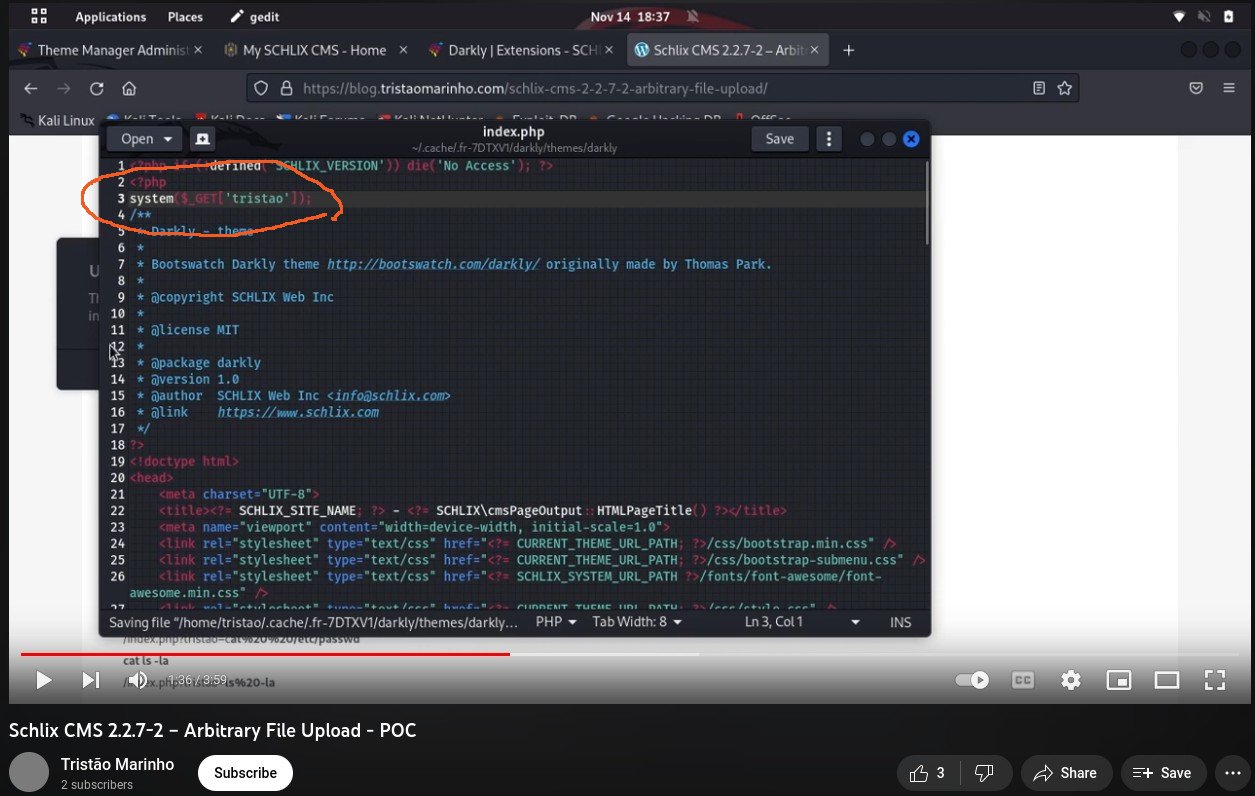
- Our response: You can add any code here because it's a PHP script. You can execute system ("rm -rf /") or whatever and it will call the system(...) function unless you disable it via php.ini.
- Zip theme_superhero-1.1.zip
- Click in "INSTALL A PACKAGE"
- Our response: It prompts for the admin password again and there is a warning to upload files only from a trusted source and that we're not responsible for any security vulnerability caused by 3rd party plugins. This is why we put the warning here. People who have access to this are usually web developers who know what they're doing.
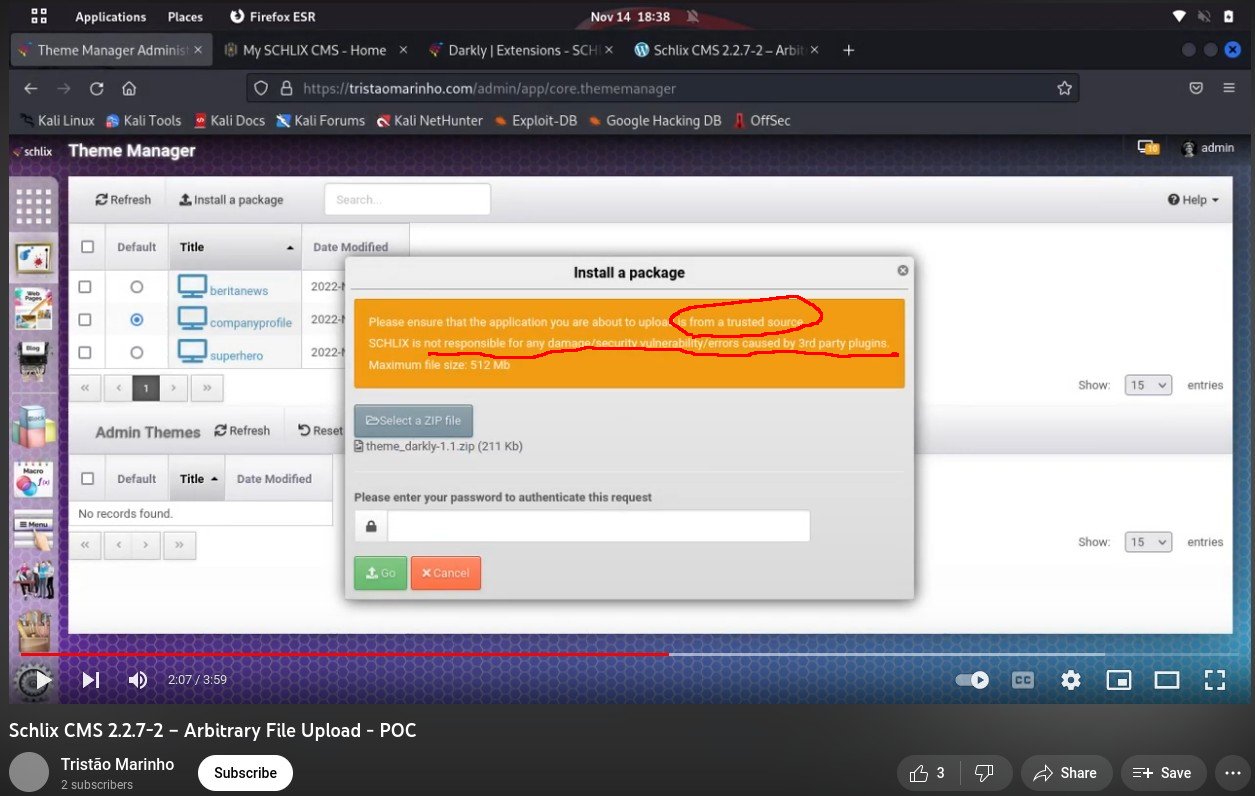
- Our response: It prompts for the admin password again and there is a warning to upload files only from a trusted source and that we're not responsible for any security vulnerability caused by 3rd party plugins. This is why we put the warning here. People who have access to this are usually web developers who know what they're doing.
- Upload theme_superhero-1.1.zip
- Active theme superhero
- Acess homepage index.php
Our response: You are an admin of this website and you put an arbitrary code in the theme file, which is index.php, and you should be able to execute it. This behaviour is the same whether you use Wordpress, Drupal, Joomla, or SCHLIX CMS.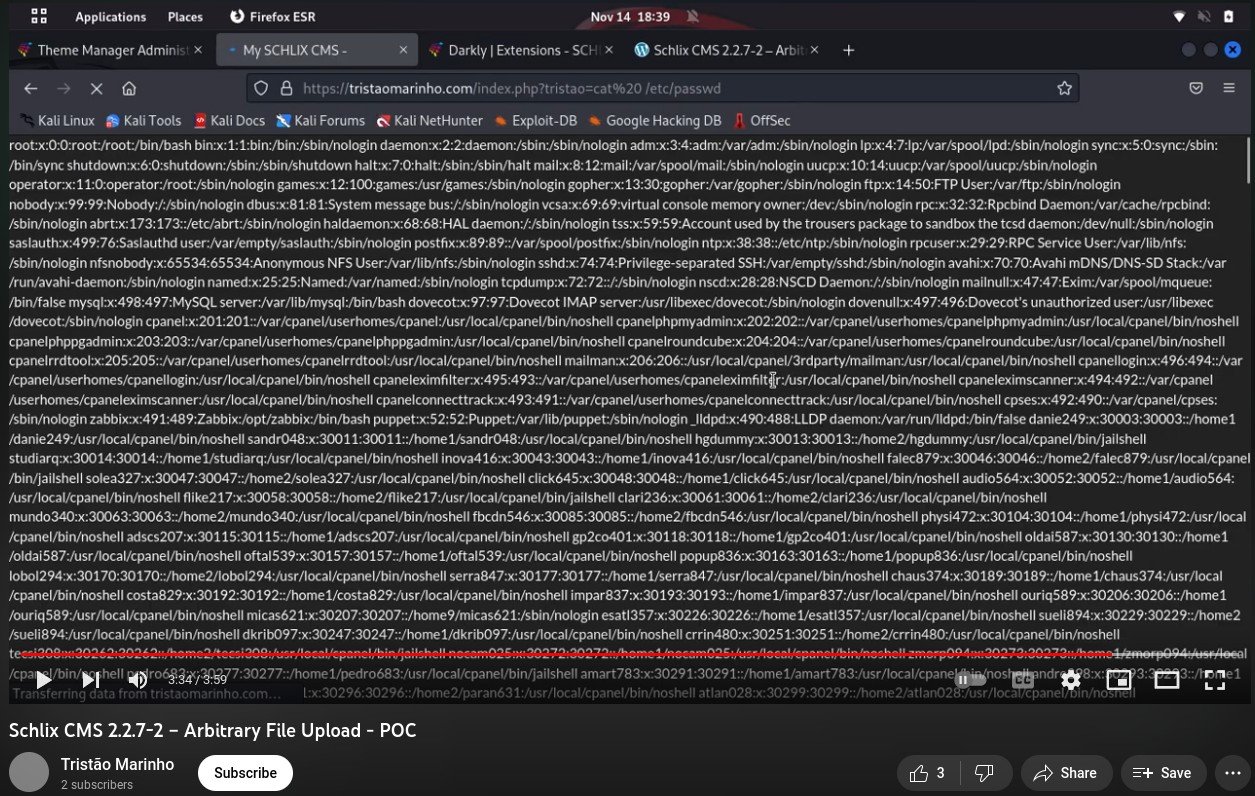
Not only the analysis is faulty and demonstrated a lack of due dilligence and programming knowledge on the so called "pentester" part, we weren't even contacted to verify his claim, which is usually the standard procedure for reporting a vulnerability. We have dealt with much more professional and knowledgable individuals in the past and we will acknowledge if there is a vulnerability, but Francisco's analysis for CVE-2022-45544 is completely faulty.
It's best for security researchers to contact us first to validate a vulnerability before publishing it.
Continue ReadingIn regards to CVE-2019-11021 for older SCHLIX CMS v2.1.8-7 (November 2018 - last year), which claimed that "admin/app/mediamanager in Schlix CMS 2.1.8-7 allows Authenticated Unrestricted File Upload, leading to remote code execution.", the analysis needs to also mention that the user who can access admin area will require an elevated superuser permission (the user must belong to [Administrators]before he/she can upload the PHP file. We also allow uploading of zipped PHP scripts to install extensions, by the way, and it's still the case even in 2.2.x.
While inadvertently allowing a PHP file to be uploaded via Media Manager was an oversight, it still requires an admin permission. We think it's pretty rare for an administrator to exploit a bug on his/her own site to own his/her own site.
It's best for security researchers to contact us first to validate a vulnerability before publishing it. Regardless, we still thank for the effort.
For SCHLIX CMS users, simply click Settings - System Update to keep your system secure all the time. Also, subscribe to this RSS news feed for the latest news including security related advisories.
Continue Reading